Seamless User Management Migration: Future-Proofing with Azure
Executive Summary
We successfully migrated a multi-tenant system without downtime, improving scalability and eliminating technical debt. The key benefits were:
- Eliminated dependency on unsupported Microsoft Membership framework
- Enabled cloud scalability via Azure App Service deployment
- Created a centralized identity management architecture
- Maintained system availability with zero disruption for tenants
- Established a foundation for future feature expansion
The migration was accomplished with minimal risk through careful planning, proof-of-concept validation, and robust fallback mechanisms that proved invaluable during deployment.
Client Challenge
Legacy System Limitations
The client ran a complex multi-tenant app ecosystem. It included a User Management system based on outdated technology:
- Microsoft Membership: No longer supported in modern .NET environments
- Distributed Authentication: Multiple modules each maintaining separate login pages
- Technical Debt: Growing maintenance overhead and security concerns
- Feature Implementation Challenges: Required redundant updates across multiple modules, increasing maintenance overhead
- Scalability Constraints: Legacy system hosted on VM-based IIS without auto-scaling capabilities
Business Objectives
The client sought to:
- Reduce technical debt by eliminating deprecated technology
- Centralize identity management capabilities
- Streamline engineering efforts for future feature implementations
- Improve scalability to handle variable demand
- Maintain system stability throughout the transition
Solution Approach
Assessment & Strategy
After I finished analyzing the current applications, APIs, and dependencies, I crafted a migration strategy that focused on:
✅ Minimal Disruption: Ensuring tenant applications remained functional throughout the transition.
✅ Phased Implementation: Breaking the migration into manageable segments to reduce risk.
✅ Fallback Mechanisms: Building safety nets to ensure business continuity.
✅ Database Compatibility: Preserving existing schema where possible to minimize disruption.
Why This Approach?
To ensure a seamless transition, we prioritized solutions that required minimal changes for end-users while maximizing scalability. Here’s what guided our approach:
Key Strategic Decisions
Several critical decisions shaped the migration approach:
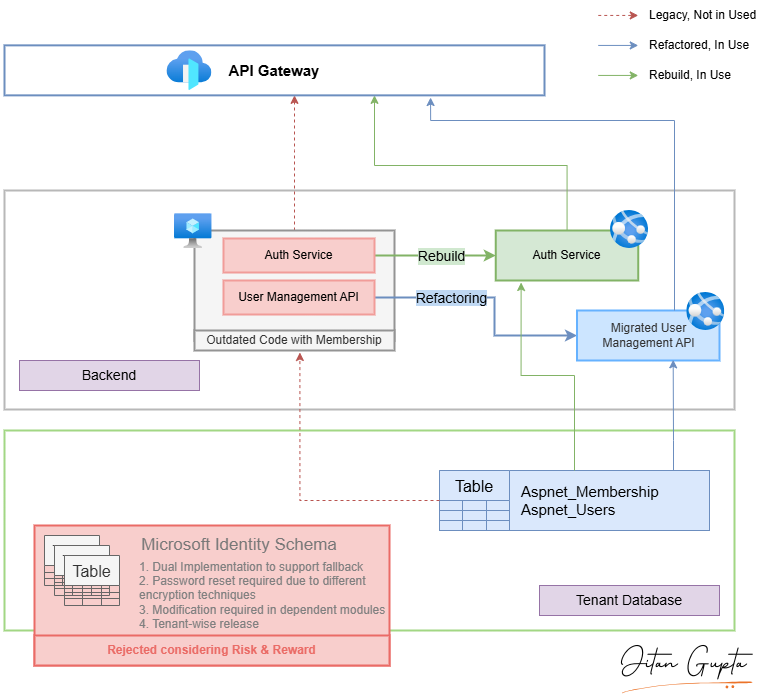
- Why We Rejected a Full Identity Migration: Despite its modern features, Microsoft Identity wasn’t the best fit because:
- All users would have been forced to reset passwords.
- Dual implementation was needed during transition, complicating development.
- Dependent modules required extensive modifications.
- Custom Identity Server Implementation: Rather than adopting a third-party identity provider that required complex data migration, I created a centralized identity layer. This layer is built on our newly migrated authentication service.
- Code Rebuild vs. Refactor: We rebuilt the authentication service while preserving existing interfaces, ensuring dependent systems remained unaffected. This allowed us to modernize the core without disrupting external integrations.
Migration Roadmap
The migration plan included:
- Initial assessment and proof-of-concept validation
- Stakeholder presentations and approval process
- Phased implementation with built-in fallback mechanisms
- Gradual elimination of Membership dependencies
- Strategic preservation of database structure
- Development of centralized identity layer
Technical Implementation
Phase 1: Authentication Service Migration
- Rebuilt authentication service in .NET Core while maintaining identical payload and response bodies
- Implemented robust fallback mechanism to legacy service
- Released new service with zero disruption to dependent systems
Phase 2: API Modernization
- Migrated User Management APIs from .NET Framework to .NET Core
- Eliminated Membership code dependencies while preserving database structure
- Leveraged existing .NET Core service infrastructure
Phase 3: Centralized Identity Implementation
- Developed UI layer on top of authentication service
- Consolidated login and SSO capabilities into centralized service
- Created foundation for unified authentication across all modules
Challenges & Solutions
Deployment Challenge
Challenge: After initial deployment, the migrated system experienced unexpected issues leading to system failure.
Solution: The fallback mechanism restored service quickly, within minutes. This shows the importance of smart risk planning.
Database Schema Challenge
Challenge: Changing the database schema means updating each tenant’s database. This could cause major disruptions.
Solution: Keep the current database structure. Remove code dependencies. This balances reducing technical debt with managing implementation risk.
User Experience Considerations
Challenge: Migrations often cause login issues and force password resets, frustrating users. Our goal was a frictionless experience.
Solution:
- Preserved Login Experience: The new authentication system maintained existing login endpoints and payload structures to ensure dependent applications continued to function without modification.
- Zero Forced Password Resets: Users could continue using their existing credentials without needing to reset passwords, avoiding unnecessary friction.
- Minimal User Impact Strategy: Since the migration focused on backend improvements, users experienced no change in their authentication experience.
- Proactive Monitoring: I closely monitored login requests post-migration to detect anomalies and ensure a seamless transition.
Business Impact
Immediate Wins
- Eliminated Legacy Dependencies: Removed reliance on unsupported Microsoft Membership.
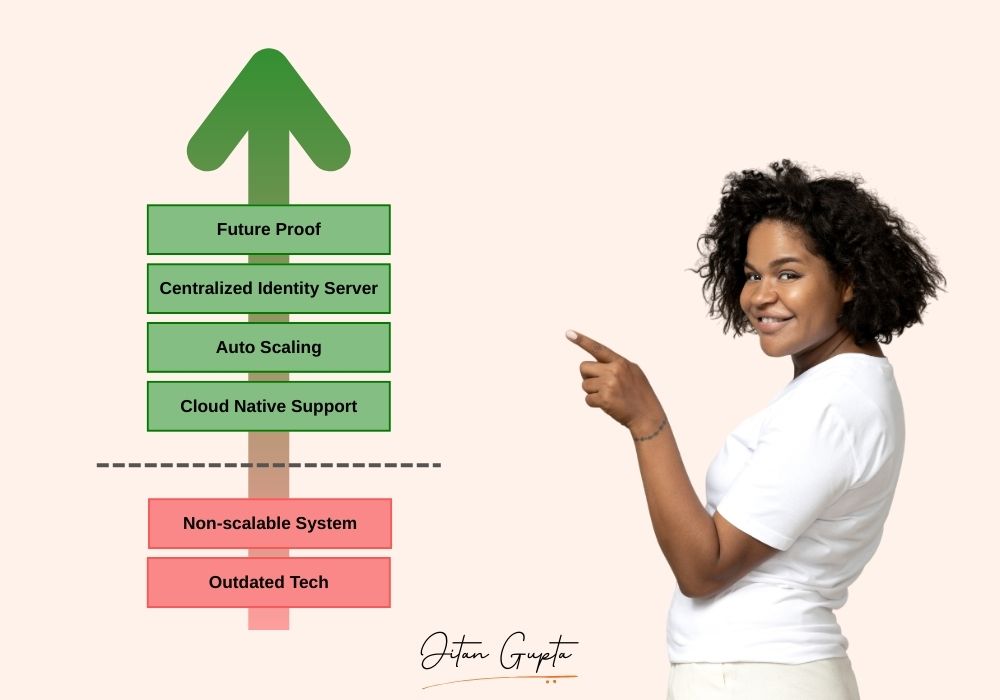
- Cloud-Ready Architecture: New implementation deployed on Azure App Service with auto-scaling capabilities.
- Improved System Resilience: Fallback mechanisms proved effective during deployment challenges.
Long-Term Gains
- Reduced Operational Risk: By removing deprecated technology, we minimized security vulnerabilities and long-term stability risks.
- Improved Scalability: Azure App Service deployment automatically scales to meet demand fluctuations.
- Engineering Efficiency: Centralized identity management reduces duplicate implementation efforts for new features.
- Future-Ready Foundation: Architecture supports addition of modern authentication features like 2FA.
Future Enhancements
Next, we’re enhancing the UI authentication flow and expanding SSO, making access even smoother.
Facing similar migration challenges? Let’s discuss your architecture.
 R██████ ███████
Senior Director of Engineering, ████████████
R██████ ███████
Senior Director of Engineering, ████████████ 